2021 Roundup Of AI And Machine Learning Market Forecasts Show Strong Growth

- Forrester forecasts that the size of the AI software market will approach $37 billion by 2025.
- IDC predicts the worldwide artificial intelligence (AI) market, including software, hardware, and services, will grow from $327.5 B in 2021 to $554.3B in 2024 with a five-year compound annual growth rate (CAGR) of 17.5%.
- By 2024, 70% of enterprises will use cloud and cloud-based AI infrastructure to operationalize AI, thereby significantly alleviating concerns about integration and upscaling, according to Gartner’s data and analytics predictions for 2021.
- By 2025, 50% of enterprises will have developed AI orchestration platforms to operationalize AI — up from fewer than 10% in 2020, according to a recent study by Gartner.
Demand for TensorFlow expertise is one of the leading indicators of machine learning and AI adoption globally. Kaggle’s State of Data Science and Machine Learning 2020 Survey found that TensorFlow is the second most used machine learning framework today, with 50.5% of respondents currently using it.
TensorFlow expertise continues to be one of the most marketable machine learning and AI skills in 2021, making it a reliable leading indicator of technology adoption. In 2020, there were on average 4,134 LinkedIn open positions that required TensorFlow expertise soaring to 8,414 open LinkedIn positions this year in the U.S. alone. Globally, demand for TensorFlow expertise has doubled from 12,172 open positions in 2020 to 26,958 available jobs on LinkedIn today.
Demand for machine learning expertise, as reflected in LinkedIn open positions, also shows strong growth. Increasing from 44,864 available jobs in 2020 to 78,372 in 2021 in the U.S. alone, organizations continue to staff up to support new initiatives quickly. Globally, LinkedIn’s open positions requiring machine-learning expertise grew from 98,371 in 2020 to 191,749 in 2021.
Market forecasts and projections also reflect strong growth for AI and machine learning spending globally for the long term. The following are key takeaways from the machine learning market forecasts from the last year include the following:
- Forrester says the AI market will be defined and grow within four software segments, with AI maker platforms growing the fastest, reaching $13 billion by 2025, helping drive the market to $37 billion by 2025. Forrester is defining the four AI software segments as follows: AI maker platforms for general-purpose AI algorithms and data sets; AI facilitator platforms for specific AI functions like computer vision; AI-centric applications and middleware tools built around AI for specialized tasks like medical diagnosis; and AI-infused applications and middleware tools that differentiate through advanced use of AI in an existing app or tool category. New AI-centric apps built on AI functions such as medical diagnosis and risk detection solutions will be the second-largest market, valued at nearly $10 billion by 2025. Source: Sizing The AI Software Market: Not As Big As Investors Expect But Still $37 Billion By 2025, December 10, 2020.

- IDC predicts worldwide revenues for the artificial intelligence (AI) market, including software, hardware, and services, will grow from $327.5 billion in 2021 to $554.3 billion in 2024, attaining a five-year compound annual growth rate (CAGR) of 17.5%. IDC further predicts that the AI Software Platforms market will be the strongest, with a five-year CAGR of 32.7%. The slowest will be AI System Infrastructure Software, with a five-year CAGR of 13.7% while accounting for roughly 36% of AI software revenues. IDC found that among the three technology categories, software represented 88% of the total AI market revenues in 2020. It’s the slowest growing category with a five-year CAGR of 17.3%. AI Applications took the largest share of revenue within the AI software category at 50% in 2020. Source: IDC Forecasts Improved Growth for Global AI Market in 2021, February 23, 2021

- AI projects continued to accelerate in 2020 in the healthcare, bioscience, manufacturing, financial services, and supply chain sectors despite economic & social uncertainty. Two dominant themes emerge from the combination of 30 diverse AI technologies in this year’s Hype Cycle. The first theme is the democratization or broader adoption of AI across organizations. The greater the democratization of AI, the greater the importance of developers and DevOps to create enterprise-grade applications. The second theme is the industrialization of AI platforms. Reusability, scalability, safety, and responsible use of AI and AI governance are the catalysts contributing to the second theme. The Gartner Hype Cycle for Artificial Intelligence, 2020, is shown below: Source: Software Strategies Blog, What’s New In Gartner’s Hype Cycle For AI, 2020, October 20, 2020.

- Capgemini finds that Life Sciences, Retail, Consumer Products, and Automotive industries lead in the percentage of successfully deployed AI use cases today. Life Sciences leads all interviewed industries to AI maturity, with 27% of companies saying they have deployed use cases in production and at scale. Retail is also above the industry average of 13% of companies that have deployed AI in production at scale, with 21% of companies in the industry has adopted AI successfully. 17% of companies in the Consumer Products and Automotive industries now have AI in production, running at scale. Source: Capgemini, Making AI Work For You, (The AI-powered enterprise: Unlocking the potential of AI at scale) 2021

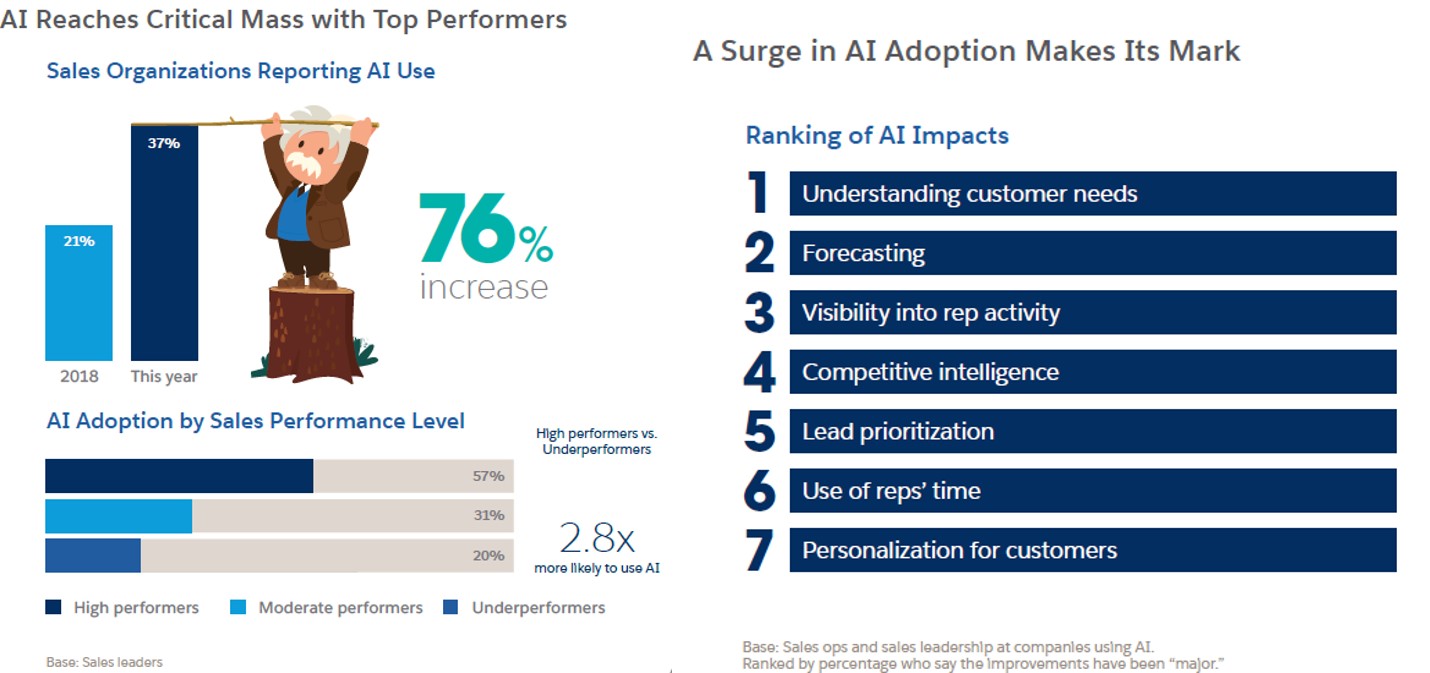
- Between 2018 and 2020, there’s been a 76% increase in sales professionals using AI-based apps and tools. Salesforce’s latest State of Sales survey found that 57% of high-performance sales organizations use AI today. High-performing sales organizations are 2.8x more likely to use AI than their peers. High-performing sales organizations rely on AI to gain new insights into customer needs, improve forecast accuracy, gain more significant visibility of rep activity, improve competitive analysis, and more. Source: Salesforce Research, 4th Edition, State of Sales, June 2020
- While 24% of companies are currently using AI for recruitment, that number is expected to grow, with 56% reporting they plan to adopt AI next year. In addition, Sage’s recent survey of 500 senior HR and people leaders finds adoption of AI as an enabling technology for talent management increasing. AI is proving effective for evaluating job candidates for potential, improving virtual recruiting events, and reducing biased language in job descriptions. It’s also proving effective in helping to improve career planning and mobility. Josh Bersin, a noted HR industry analyst, educator, and technologist, recently published an interesting report on this area titled The Rise of the Talent Intelligence Platform. Leaders in the field of Talent Intelligence Platforms include Eightfold.ai. Grounded in Equal Opportunity Algorithms, the Eightfold® Talent Intelligence Platform uses deep-learning AI to help each person understand their career potential, and each enterprise understands the potential of their workforce.Sources: VentureBeat, 8 ways AI is transforming talent management in 2021, March 25, 2021, and Eightfold.ai.

- 84% of marketers are using AI-based apps and platforms today, up from 28% in 2018. Salesforce Research’s latest State of Marketing survey finds that high-performing marketers use an average of seven different applications or use cases. The familiarity high-performing marketers have with AI is a primary factor in 52% of them predicting they will increase their use of AI-based apps in the future. Source: Salesforce Research, 6th Edition, State of Marketing, June 2020

- Marketing and Sales lead revenue increases due to AI adoption, yet lag behind other departments on cost savings. 40% of the organizations McKinsey interviewed see between a 6 and 10% increase in revenue from adopting AI in their marketing and sales departments. Adopting Ai to reduce costs delivers the best manufacturing and supply chain management results based on the McKinsey survey results. Revenue increases and cost reductions based on AI adoption are shown in the graphic below. Source: McKinsey & Company, The state of AI in 2020, November 17, 2020

- AI sees the most significant adoption by marketers working in $500M to $1B companies, with conversational AI for customer service as the most dominant. Businesses with between $500M to $1B lead all other revenue categories in the number and depth of AI adoption cases. Just over 52% of small businesses with sales of $25M or less use AI for predictive analytics for customer insights. It’s interesting to note that small companies are the leaders in AI spending, at 38.1%, to improve marketing ROI by optimizing marketing content and timing. Source: The CMO Survey: Highlights and Insights Report, February 2019. Duke University, Deloitte, and American Marketing Association. (71 pp., PDF, free, no opt-in).

- Three out of four companies are fast-tracking automation initiatives, including AI. Bain & Company found that executives would like to use AI to reduce costs and acquire new customers, but they’re uncertain about the ROI and cannot find the talent or solutions they need. Bain research conducted in 2019 found that 90% of tech executives view AI and machine learning as priorities that they should be incorporating into their product lines and businesses. But nearly as many (87%) also said they were not satisfied with their Company’s current approach to AI. Source: Bain & Company, Will the Pandemic Accelerate Adoption of Artificial Intelligence? May 26, 2020

- Gartner’s Magic Quadrant for Data Science and Machine Learning Platforms predicts a continued glut of exciting innovations and visionary roadmaps from competing vendors. Competitors in the Data Science and Machine Learning (DSML) market focus on innovation and rapid product innovation over pure execution. Gartner said key areas of differentiation include UI, augmented DSML (AutoML), MLOps, performance and scalability, hybrid and multicloud support, XAI, and cutting-edge use cases and techniques (such as deep learning, large-scale IoT, and reinforcement learning). Please see my recent article on VentureBeat, Gartner’s 2021 Magic Quadrant cites ‘glut of innovation’ in data science and ML, March 14, 2021.

- 76% of enterprises are prioritizing AI & machine Learning In 2021 IT Budgets. Algorithmia’s survey finds that six in ten (64%) organizations say AI and ML initiatives’ priorities have increased relative to other IT priorities in the last twelve months. Algorithmia’s survey from last summer found that enterprises began doubling down on AI & ML spending last year. The pandemic created a new sense of urgency regarding getting AI and ML projects completed, a key point made by CIOs across the financial services and tech sectors last year during interviews for comparable research studies. Source: Algorithmia’s Third Annual Survey, 2021 Enterprise Trends in Machine Learning.

- Technavio predicts the Artificial Intelligence platforms market will grow to $17.29 billion by 2025, attaining a compound annual growth rate (CAGR) of nearly 35%. The research firm cites the increased levels of AI R&D investments globally combined with accelerating adoption for pilot and proof of concept testing across industries. Technavio predicts Alibaba Group Holding Ltd., Alphabet Inc., and Amazon.com Inc. will emerge as top artificial intelligence platforms vendors by 2025. Source: Artificial Intelligence Platforms Market to grow by $ 17.29 Billion at 35% CAGR during 2021-2025. June 21, 2021

- Tractica predicts the AI software market will reach $126 billion in worldwide revenue by 2025. The research firm predicts AI will grow fastest in consumer (Internet services), automotive, financial services, telecommunications, and retail industries. As a result, annual global AI software revenue is forecast to grow from $10.1 billion in 2018 to $126.0 billion by 2025. Source: T&D World, AI Software Market to Reach $126.0 Billion in Annual Worldwide Revenue by 2025.
Sources of Market Data on Machine Learning:
- Algorithma, 2020 state of enterprise machine learning, Nov. 2019 (PDF, 29 PP., no opt-in)
- Accenture, Machine Learning In Insurance (PDF, 14 pp., no opt-in)
- Ark Invest Big Ideas 2019, Innovation is the Key To Growth (PDF, 94 pp., no opt-in)
- Artificial Intelligence: Emerging Opportunities, Challenges and Implications. U.S. Government Accountability Office, March 2018 (PDF, 100 pp., no opt-in)
- Artificial Intelligence in Europe: How 277 Major Companies Benefit from AI Outlook for 2019 and Beyond by Ernst & Young (PDF, 41 pp., no opt-in)
- Artificial Intelligence Index, 2018 Annual Report (PDF, 94 pp., no opt-in)
- Boston Consulting Group, AI at Scale: The Next Frontier in Digital Transformation
- Capgemini, Accelerating Automotive’s AI transformation: How driving AI enterprise-wide can turbo-charge organizational value, March 2019. PDF of the study is available here (PDF, 36 pp.., no opt-in)
- Chamakkala, Vipin, Today’s AI Software Infrastructure Landscape (And Trends Shaping The Market) Medium. May 7, 2018
- Deloitte, State of AI in the Enterprise, 2nd Edition, Early adopters combine bullish enthusiasm with strategic investments (PDF, 28 pp., no opt-in)
- Forbes, 10 Ways Machine Learning Is Revolutionizing Sales, December 26, 2018
- Forbes, How China Is Dominating Artificial Intelligence, December 16, 2018
- Forbes, How To Improve Supply Chains With Machine Learning: 10 Proven Ways, April 28, 2019
- Forbes, Microsoft Leads The AI Patent Race Going Into 2019, January 6, 2019
- IDC Worldwide Artificial Intelligence Market Shares, 2018: Steady Growth — POCs Poised to Enter Full-Blown Production
- IDC Worldwide Spending on Cognitive and Artificial Intelligence Systems Forecast to Reach $77.6 Billion in 2022, According to New IDC Spending Guide.
- The Economist, Risks and Rewards, Scenarios around the economic impact of machine learning (PDF, 80 pp., no opt-in)
- McKinsey, An Executive’s Guide to AI
- McKinsey Global Institute, Tackling Europe’s gap in digital and AI, February 2019 Discussion paper
- McKinsey Global Institute, Applying artificial intelligence for social good, November, 20-8 discussion paper
- McKinsey Global Institute, Notes from the AI Frontier: Tackling Europe’s Gap In Digital and AI (PDF, 60 pp., no opt-in)
- McKinsey Global Institute, Notes from the AI frontier: Applications and value of deep learning, April 2018
- McKinsey Global Institute, Visualizing the uses and potential impact of AI and other analytics, April 2018
- MIT Sloan Management Review, Artificial Intelligence in Business Gets Real: Pioneering Companies Aim for AI at Scale, September 17, 2018, PDF available here.
- Stanford University, Artificial Intelligence Index Report 2019, (PDF, 291 PP., no opt-in)
- Statista, In-Depth: Artificial Intelligence 2019, February 2019
- Statista, Machine Learning Tops AI Dollars, May 10, 2019.
- Tractica, Artificial Intelligence: 10 Predictions for 2019 (PDF, 12 pp., no opt-in)
- U.S. Government Accountability Office, AI technology Assessment, Emerging Opportunities, Challenges, and Implications (PDF, 100 pp., no opt-in)
- World Economic Forum, How to Prevent Discriminatory Outcomes in Machine Learning (PDF, 30 pp., no opt-in)
- Stanford University’s Institute for Human-Centered Artificial Intelligence, the Artificial Intelligence Index Report 2021, (PDF, 222 PP., no opt-in)
- The Economist, An understanding of AI’s limitations is starting to sink in, June 13, 2020
- PWC, AI Predictions 2021, June 2021

























